Identity Status Check
The moment you sign up we’re able to run a comprehensive
check on your information and make you aware of any
previous or ongoing instances of ID theft.
We scan for signs of crimes committed in your name by monitoring 500 million criminal court records, 60 million incarceration records, and 99 million Department of Corrections records.
We send you notifications for bank account applications, newly opened bank accounts, bank account takeovers, credit card applications, and new credit card openings.
Complete ID monitors online properties to identify the illegal trading and selling of your personal information. Your first Dark Web Surveillance Report checks millions of compromised information found on the dark web.
Identity thieves will often forward your mail so we’ll send you notifications when the USPS processes a mail change alert associated with your name.
Complete ID uses state sex offender registries to make you aware of offenders in your area. You’ll have the power to make informed decisions to keep yourself and your family safe.
Alternative Loan Monitoring notifies you of any alternative lending activity associated with your monitored personal info. Alternative lending includes online or storefront activity such as: payday loans, installment loans, single payment loans, auto loans, rent-to-own, lines of credit, title loans, and credit cards.
Get alerts for any name or address associated with your SSN. If a name or address is being used fraudulently, our specialists can help you contact the social security office, review your credit report, and place a fraud alert or security freeze with the three major credit bureaus.
Our monitoring features scan the most crucial information including your credit and debit cards, SSN, email address, medical ID, passport, driver’s license, bank accounts, and phone number.
Spotting a quality monitoring service
HOW IS COMPLETE ID DIFFERENT FROM FREE CREDIT MONITORING SERVICES?
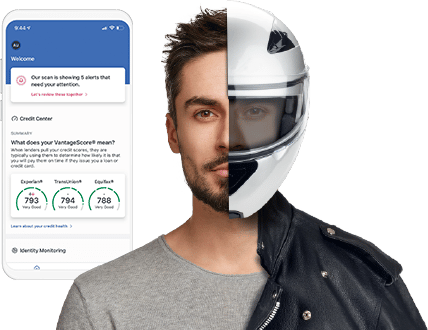
Many financial services will tack on complimentary credit monitoring alerts, but these free services can only alert you to credit-related theft, leaving you only partially protected.
Complete ID helps protect from every angle with comprehensive screening and assistance in identity restoration.
Identity theft can happen anytime, anywhere
Get More with Complete ID
Identity protection, Credit Monitoring & Scoring, and Restoration
Credit Monitoring
and Scoring
play_arrow Learn More
Restoration
Services
play_arrow Learn More
*All plan pricing is subject to applicable sales tax. Service provided by Experian®.